New phishing tactics, advice on how to protect yourself, and measures you can take as a company should you be targeted.
Phishing – where malicious third parties disguise themselves as a trustworthy entity to get you to provide usernames, passwords and credit card details – is on the increase.
In the first quarter of 2016, phishing attacks surged by 250%, according to a report from APWG.
Chairman Dave Jevans noted the attackers’ increased aggressiveness and sophistication – these examples showing attacks on Google Drive and Dropbox illustrate how far they’ve come from the days of sending poorly written emails posing as banks.
Esendex customer accounts have also been targeted, and so this post aims to alert you to some of the new tactics in play, advise you on how to protect yourself, and what measures you can take as a company should you also be targeted.
Look out for unusual domain name endings
As at March 2016, there were 882 domain extensions – this infographic lists them all – and while any of them *could* be used for legitimate business, they do present an opportunity for hackers to pass themselves off as a legitimate business.
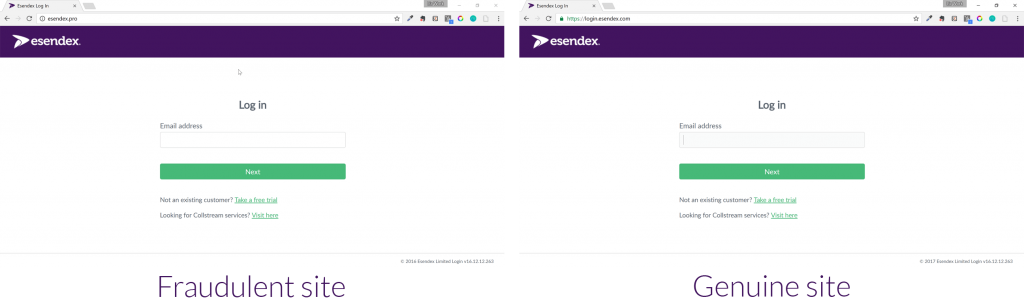
We’ve seen this at Esendex, with hackers purchasing .pro, .me and .top domain extensions to attempt to fool customers into thinking that the website they’ve landed on belongs to Esendex. They’ll do a pretty convincing job of it, too, lifting the styling from your website so it looks virtually identical.
As you can see, there’s little to choose between them if you’re not paying attention – the domain name, the use of https and the lock symbol, and the copyright notice are the only differentiating marks.
Your options for preventing this are fairly limited: you can report abuse to the domain name registrar (use https://www.whois.net/ to find out who the registrar is), and they *should* take the fraudulent website down (some registrars are more responsive than others though!).
However the most sustainable course of action is education: make your customers aware of the issue, and make sure they know the correct URL to access your services.
For the record, Esendex’s services should only be accessed via our brochure site at https://www.esendex.co.uk/ (using the login button at the top right), or directly at https://login.esendex.com/.
Takeaway point: stick to recognisable domain extensions such as .co.uk and .com.
Don’t place blind trust in Google Ads
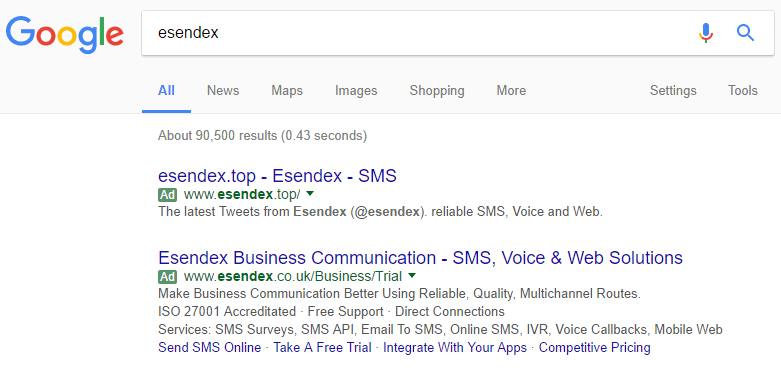
Like a lot of companies, Esendex bids on our own brand name in Google Adwords, so that when someone searches for ‘Esendex’, they will see Esendex at the top of the results as a sponsored link (indicated by the green ‘Ad’ button).
However, there is nothing to stop a third party from also bidding on Esendex’s brand name, or your brand name; Google lifted the restriction preventing companies from doing this several years ago, and it can lead to a result like this:
Whether you use Google Adwords or not, this is something to be aware of. Bitcoin was heavily targeted by this tactic in 2016, and ironically even Google Adwords itself has had a similar experience.
If you use Adwords, you can set up alerts to advise you if someone has outbid you on your brand name, and you can automatically increase your bid to redress the balance.
You can and should report the activity to Google, who will take action to close the scammer’s Adwords account.
Google shut down 7,000 phishing sites in 2015, and I’d be surprised if that figure wasn’t significantly higher in 2016.
Again, educate your customers to access your services via a bookmarked website rather than using a search engine, and you’ll remove the scammer’s ability to phish for details this way.
Change your password regularly
https://haveibeenpwned.com/ is a useful resource to check whether your email address has been caught up in one of the much publicised hacks of recent years.
It checks stolen databases to see if your email’s among them, and if it is, this is a clear warning sign that you should change your password for all online services.
But it’s simple best practice to:
- Change your password every six months
- Use different passwords for each online service you use
- Avoid easy to guess passwords (How to Geek has some great advice here).
Has your business experienced phishing attacks? Please share your experiences and stay safe online.